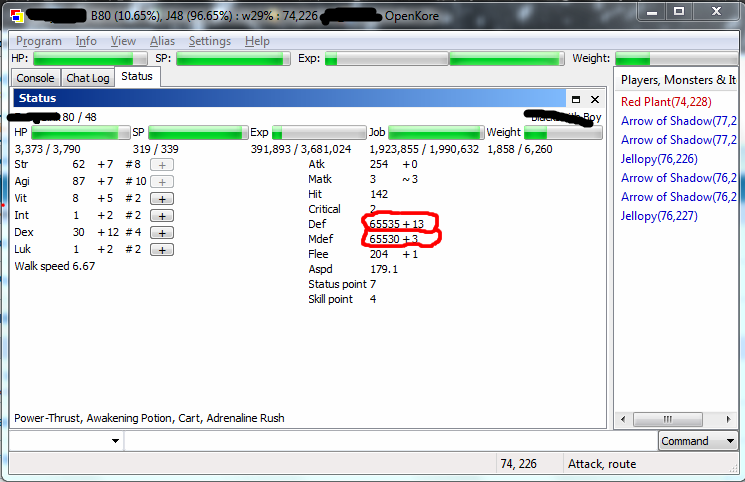
My actual stats are:
-1 +13 Def
-6 +3 MDef
Screen shot of error:
Moderators: Moderators, Developers



So lets look at the actual struct:The integer formats s, S , i , I , l , L , j , and J are inherently
non-portable between processors and operating systems because they
obey native byteorder and endianness. For example, a 4-byte integer
0x12345678 (305419896 decimal) would be ordered natively
(arranged in and handled by the CPU registers) into bytes as:
0x12 0x34 0x56 0x78 # big-endian
0x78 0x56 0x34 0x12 # little-endian
Starting with Perl 5.9.2, integer and floating-point formats, along with
the p and P formats and () groups, may all be followed by the > or < endianness
modifiers to respectively enforce big- or little-endian byte-order.
These modifiers are especially useful given how n , N , v and V don't cover
signed integers, 64-bit integers, or floating-point values
Code: Select all
// packet 0xbd
struct PACKET_ZC_STATUS {
/* this+0x0 */ short PacketType
/* this+0x2 */ short point
/* this+0x4 */ unsigned char str
/* this+0x5 */ unsigned char standardStr
/* this+0x6 */ unsigned char agi
/* this+0x7 */ unsigned char standardAgi
/* this+0x8 */ unsigned char vit
/* this+0x9 */ unsigned char standardVit
/* this+0xa */ unsigned char Int
/* this+0xb */ unsigned char standardInt
/* this+0xc */ unsigned char dex
/* this+0xd */ unsigned char standardDex
/* this+0xe */ unsigned char luk
/* this+0xf */ unsigned char standardLuk
/* this+0x10 */ short attPower
/* this+0x12 */ short refiningPower
/* this+0x14 */ short max_mattPower
/* this+0x16 */ short min_mattPower
/* this+0x18 */ short itemdefPower
/* this+0x1a */ short plusdefPower
/* this+0x1c */ short mdefPower
/* this+0x1e */ short plusmdefPower
/* this+0x20 */ short hitSuccessValue
/* this+0x22 */ short avoidSuccessValue
/* this+0x24 */ short plusAvoidSuccessValue
/* this+0x26 */ short criticalSuccessValue
/* this+0x28 */ short ASPD
/* this+0x2a */ short plusASPD
}in C:n An unsigned short (16-bit) in "network" (big-endian) order.
C An unsigned char (octet) value.
s A signed short (16-bit) value.
Code: Select all
'00BD' => ['stats_info', 's< C12 s14<', [qw(points_free str points_str agi points_agi vit points_vit int points_int dex points_dex luk points_luk attack attack_bonus attack_magic_min attack_magic_max def def_bonus def_magic def_magic_bonus hit flee flee_bonus critical karma manner)]],